Assets

Exchange

Buy Crypto

Products




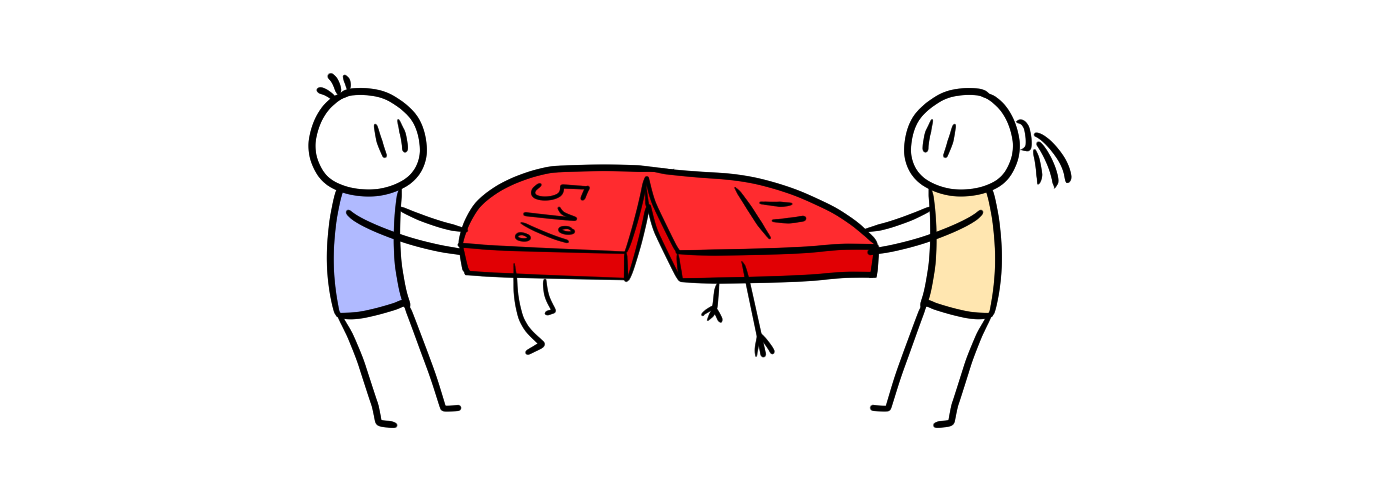
Blockchain-based cryptocurrencies are a subject to the so-called attack of 51%: when more than half of the computing power of a cryptocurrency network is controlled by some organization or group of individuals, it becomes possible to conduct conflicting transactions or malicious harm.
A 51% attack is a potential Bitcoin attack (or attack on another blockchain network), with the result that one organization can control most of the hash rate. Such a situation can lead to network failure. In other words, an attacker with a 51% hash rate has enough power to deliberately exclude or reorder transactions.
A 51% attack allows an attacker to reverse transactions that were carried out at the time of control, which is likely to lead to the problem of double-spending. A successful majority attack will also allow an attacker to prevent some or all transactions from being confirmed (also known as a denial of service), or to prevent the mining of some or all other miners, leading to the so-called mining monopoly.
On the other hand, the majority attack won’t allow an attacker to reverse transactions of other people or prevent the distribution of transactions in the network. Changing a block’s reward, creating coins from the air, or stealing coins that an attacker never had, is also an incredible scenario. A 51% attack can be carried out only in blockchains with a Proof-of-Work algorithm consensus.
Proof-of-Work (PoW) is the first successful decentralized consensus algorithm in the blockchain. PoW is used in Bitcoin, Ethereum (Ethereum plans to upgrade to Proof-of-Stake), Litecoin, ZCash, Monero, and many other platforms.
First, users send each other coins. Then all the transactions form blocks and are recorded in a blockchain or in a so-called decentralized registry.
All transactions are confirmed using complex mathematical calculations, the accuracy of which can be verified by any user of the network. Miners deal with the formation of a new block and transaction confirmation. If a miner has managed to solve the problem, a new block is formed: the next set of transactions is placed in it, and they are considered confirmed. Tasks become more difficult with time, due to the growing number of network users.
The greatest danger for the system is double-spending. So, an attacker who owns 51% of power can create a hidden alternative blockchain and use it to confirm his own transactions. For example, the confirmation of a transaction in the Bitcoin network requires six opened transaction blocks. Accordingly, an attacker must create six blocks. Then he withdraws his funds on the main blockchain. For example, transfers to another account or pays for the purchase, and opens his own chain of blocks, causing a conflict in the system. If both miners have found the right solution for one block, then a network is ramified, where both solutions have the right to exist and are included in the next block of transactions.
The remaining 49% of the network capacity confirms the debit of funds from the account. However, since the attacker has control power, the system recognizes his network to be faithful, in which he has not yet debited the funds, and it will discard the transaction confirmed by other miners since the attacker’s block is more complex. Accordingly, the system will show the balance before the transaction and the attacker will be able to spend money several more times, but with each subsequent time, the cost of coins will decrease.
Double withdrawal of funds is possible with less control of capacity, but a concentration of 51% provides a 100% guarantee that the attacker’s block will be recognized as the right block.
Having in hands 51% of system capacity, the attacker practically becomes the owner of the blockchain, can independently generate blocks, confirm and reject transactions. Having seized the system, he can also stop its work by refusing to confirm all transactions.
A 51% attack has four types of consequences, which can sometimes be very dangerous for network victims:
One of them is selfish mining when attackers take advantage of their majority in terms of receiving rewards. If a block is mined simultaneously, miners must vote on whose block they choose. The winner has more chances for the next block. Since most of the network must make a decision about this, an attacker can use his ability to mine his own blocks and continue mining being on the top, without waiting for network approval.
Secondly, an attacker who has a 51% majority in the network may decide to cancel transactions. He can destroy the entire network without accepting any transactions to any of the blocks that the attacker selfishly extracts.
The third consequence is a problem that every blockchain is most concerned about and seeks to avoid at all costs. You already know this because this is double-spending, which means spending the same coin on several transactions at the same time. Since the decentralized nature of the blockchain prevents double costs, an attacker with 51% has the central authority for this, since other miners are compromised. Continuous double costs will bring the value of a cryptocurrency to zero. The latter occurs when the attacker creates a hard fork on the blockchain. The reason for this may be the use of double costs arising during the separation of chains.
Alternatively, another reason could be the struggle with other miners who may have managed to create a block. In this case, the attacker can break the chain to this new block.
In 2014, the Ghash.io pool took control of 55% of the Bitcoin network. Despite the fact that this wasn’t a planned attack, and the pool voluntarily agreed to reduce the power indicators and promised not to exceed 40% of the threshold, the Bitcoin rate dropped by a quarter of the cost.
In 2016, Krypton and Shift – two cryptocurrencies operating on the Ethereum base, were attacked by a group of hackers calling themselves “Team 51”. As a result, fraudsters managed to double-debit and steal 22,000 coins through Bittrex.
The most precedent case occurred with the Verge cryptocurrency, but this attack was possible due to an error in the code. Anonymous cryptocurrency has functioned at once on several algorithms that had to change with the creation of each new block. However, the code has a bug due to which the attackers sent blocks with a false timestamp to the network.
Blocks were generated and sent every second, instead of every 30 seconds. The attack lasted three hours. Hackers managed to capture 99% of the blocks. According to official data provided by developers, it was possible to withdraw 250,000 tokens from the system fraudulently. However, according to users, the real figure reaches almost 4 million.

A 51% attack on blockchains of popular cryptocurrencies requires large investments. According to the Crypto51 website, 1 hour of 51% attack on the Bitcoin network will cost $ 355,883, on the Ethereum network – $ 98,572, and on the Ethereum Classic blockchain – $ 4,534. The cost of the attack depends on the computing power of the network.
Scientists of the Indian Institute of Technology conducted a study of blockchains of different cryptocurrencies and concluded that the bitcoin blockchain is the most secure decentralized network. According to the researchers, a 51% attack on the BTC blockchain won’t bring profit, since the network is protected from the double-spending. An attacker will only be able to add or remove transaction information from the blocks, while the coins will remain in the users’ wallets.
At the moment, to protect a cryptocurrency from the attack one should increase the popularity and power of the network, respectively, to offer new ideas and attract new audiences.
As long as mining remains profitable and there are a huge number of users in the network, it is extremely difficult to attack the system. As soon as the profit from mining becomes less than the cost of purchasing and maintaining the equipment, miners will withdraw their power from the system and the network will become vulnerable.
Another solution is the PoS algorithm. Despite the fact that the theoretical possibility of attack exists, it is absolutely not profitable. In order to take over 51% of the network, you should acquire 51% of all system tokens, which is even times higher than the cost of computing equipment. In addition, it is not a fact that developers won’t notice this in time and won’t take quick measures to neutralize the attack.
If a 51% attack is detected in time, then developers can use hardforks.
Hard fork is a fundamental change in the cryptocurrency code, after which the connection with the old software will be completely broken. During hard fork happens the creation of a new cryptocurrency and the network split.
For coin holders, hard fork isn’t essential, since in the future they will have the opportunity to transfer savings to a new system. However, for the attacker, such a solution means losing the value of the loot.

Explore the most active and profitable Polymarket categories in 2026. Learn how politics, sports, crypto, AI, and macro markets differ by liquidity, volatility, and risk — and why category choice matters as much as prediction.

Learn how sports betting with crypto works on Polymarket. See how prediction markets differ from sportsbooks, how to read odds as probabilities, explore top markets by volume, and understand the risks before trading.